Network Architecture
Network architecture is a way to analyse network data and systems. It is based on conceptual models that streamline variance among network hardware and software systems. In the video below I will introduce network security and architecture.
Open Systems Interconnection (OSI) Model in Detail
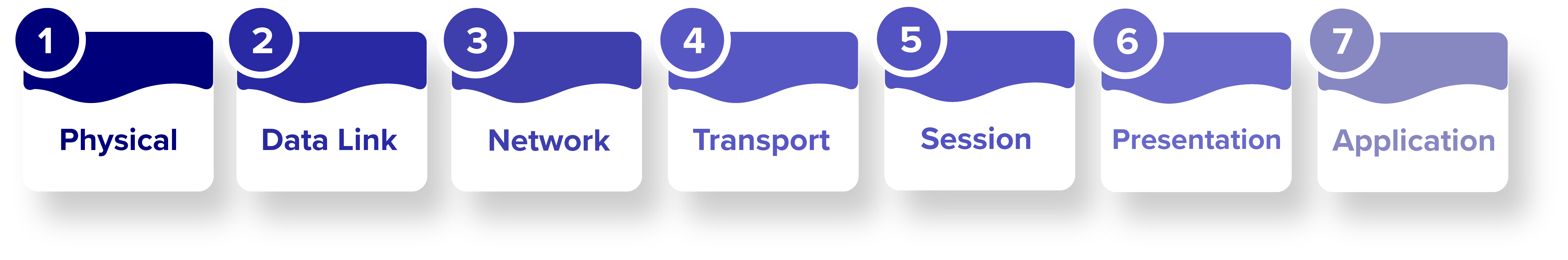
Physical: Different types of coax cables, fibres, wireless routers and hubs and switches and repeaters.
Data Link: Deals with switches and bridges and different types of network frames and ethernet based communication: Frames, ethernet, PPP, switch, bridge.
Network: Packets: IP, ICMP, IPSec, IGMP.
Transport: Deals with all sorts of security. It defines how the packets are being organised and how it is it is being sent from data link to transport layer. It handles the the IP communication of the data and sends it to the transport layer. Which provides an end-to-end connectivity using: TCP connection or UDP connection.
Session: This deals with the overall session of the communication. So, it handles synchronisation of data. It determines the ports and sockets that are required, to connect different devices all together: API's, Sockets, WinSock.
Presentation:This deals with security. Also called syntax layer. It is more of a layer that defines exactly what can be included in a in a web based environment. Dealing with server side content of the data and application level, low level data: SSL, SSH, IMAP, FTP, MPEG, JPEG.
General Network Security Architecture
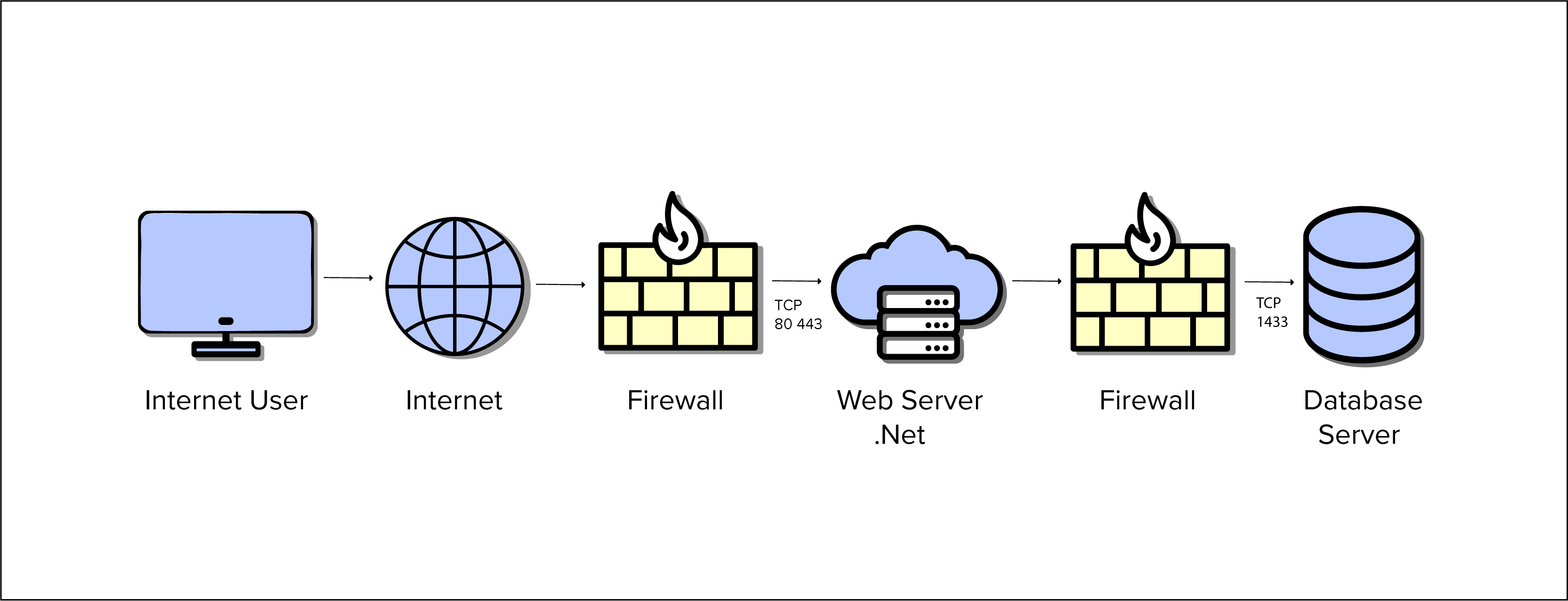
A regular user is connected to internet, assume not connected to a VPN. The user is connected to the Internet, the Internet is connected to the web server through a firewall. There are two firewalls as this is dealing with web server and database servers. These are the default ports: TCP Port 80, 443, and TCP port 1433. These are the default ports of web servers and database servers. Where exactly is security happening? At the firewall level. We define different rules based on the input, and when the data is sent to the next layer. There should be web-based server authentication, database level security. In addition, there should be separate web server authentication system working. The user first crosses the firewall successfully and upon successful movement through the firewall, it reaches a web server and may meet another layer of security before entering the second firewall. A layer of security at the database server is implemented before a user can access the data.
Watch the following video on vulnerabilities, attacks and mitigation of network security.