IoT Architecture
Internet of things is an advanced technology where billions of devices are interconnected via gateways and services, using Internet Protocol (IP). In the following short video I will introduce IoT architecture.
The Internet of Things (IoT) is the network of physical objects—devices, instruments, vehicles, buildings and other
items embedded with electronics, circuits, software, sensors and network connectivity that enables these objects to
collect and exchange data. The Internet of Things allows objects to be sensed and controlled remotely across existing
network infrastructure, creating opportunities for more direct integration of the physical world into computer-based
systems, and resulting in improved efficiency and accuracy.
A critical requirement of an IoT is that the things in the network must be inter-connected. IoT system architecture must guarantee the operations of IoT, which bridges the gap between the physical and the virtual worlds. Design of IoT architecture involves many factors such as networking, communication, business models and processes, and security. In designing the architecture of IoT, the extensibility, scalability, and interoperability among heterogeneous devices and their models should be taken into consideration. Due to the fact that things may move physically and need to interact with each other in real-time mode, IoT architecture should be adaptive to make devices interact with other things dynamically and support unambiguous communication of events.
The figure below shows a general structure of the trust zones and boundaries:
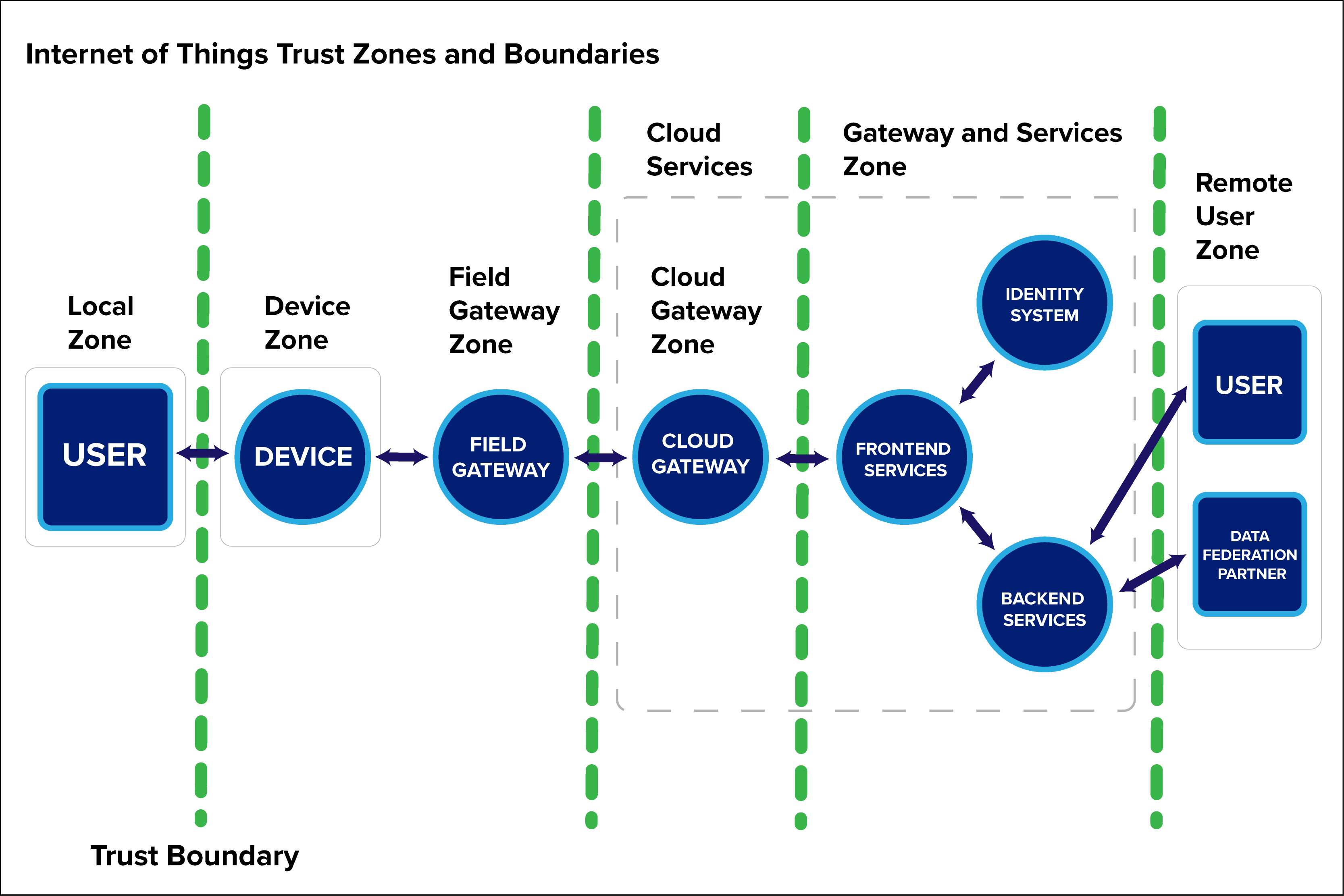
(Pietschmann, 2021) Local Zone: The Local Zone is the area where any local users will be. This could be the local or on-premises network where client computers exist, or even the physical space in close proximity to the Devices and Field Gateways. (Pietschmann, 2021)
Device Zone: The Device Zone is the area where the IoT devices are. This includes the physical space around the devices, as well as the local network the devices are connected to.
Field Gateway Zone: A Field Gateway is a component that serves as a connection point between the cloud and one or more devices and/or other field gateways.
Cloud Gateway Zone: Cloud Gateways are very similar to Field Gateways, however, instead of running on-premises or local to other devices, they run in the cloud.
Gateway and Services Zone: The Gateway and Services Zone is where all the other backend services reside. This will include databases, REST APIs, hybrid connectivity to on-premises systems, and any other backend component of the system.
Remote User Zone: The Remote User Zone is a generic container for pieces of the solution that provide some type of remote or external access to users or even third-party partners.
IoT Vulnerabilites
In the following video I will introduce the vulnerabilities, attacks and mitigation for IoT security.
Software Defined Networking (SDN)
Maintaining and securing such large scale and heterogeneous network is a challenging task. As the architecture of "things" grows traditional security mechanisms like Firewalling, Intrusion Detection and Prevention Systems, are much harder to employ as sufficient security methods as they are deployed at the Internet edge. The borderless architecture of the IoT raises additional concerns over network access control and software verification. The Software Defined Networking (SDN), offers many opportunities to protect the network in a more efficient and flexible way. In SDN architectures, network devices do not make forwarding decisions. Network devices communicate with a special node, called the SDN controller, in order to provide them with the appropriate forwarding decisions. A new device called controller connects to the switch through a secured OpenFlow channel and manages this switch via the OpenFlow protocol. In terms of security, SDN architecture extends the security perimeter to the network access end point devices (access switches, wireless access points, etc.), by pushing security policies to those devices.
Single Point of Failure
Due to the nature of SDNs, there is possibility for a single point of failure, this point is the controller. This can increase the possibility of DoS, and with control of the controller, the threat actor has access to all of the devices connected to that controller. A solution is synchronised multiple controllers. There is increased network performance with multiple controllers, because each controller has a partial view of the network, and the controllers have to collaborate and exchange informations with each other (Flauzac, 2015).The interaction between the Controller(s) and the Open-Flow enabled switches is essentially to have one Openflow switch multi-homed to multiple controllers. If one of the controllers goes down, another is ready to control the switch.
The Promise of Reliable and Secure Connectivity
The cyber landscape needs to have accountability and standards to follow, this way every company/organisation has a minimum that gives a baseline for security. With IoT impacting so many homes and businesses, the need for a widespread standard, or set of standards, is growing exponentially. Consumers need a seal of approval to guarantee their privacy is protected by brands they trust, developers need standards to help create reliable, and secure IoT devices to accelarate security positive innovation in software design. In addition, retailers need to know how to promise security for their user base (Perkins, 2022). Using standards such as Matter, or Thread in coalition could be the solution the world is looking for. One really exciting movement is the one away from "always being online", Matter allows people to use IoT devices offline. This ability to switch off smart home devices from the cloud, gives users versatility and an increased trust in their item's security.
Work Cited
Perkins, S. (2022) Matter explained: What is the next-gen smart home standard?, Android Police. Available at: https://www.androidpolice.com/matter-smart-home-standard-explained/ (Accessed: December 20, 2022).
Build with matter: Smart home device solution (2022) CSA. Available at: https://csa-iot.org/all-solutions/matter/ (Accessed: December 20, 2022).
Flauzac, O. et al. (2015) “SDN based architecture for IOT and improvement of the security,” 2015 IEEE 29th International Conference on Advanced Information Networking and Applications Workshops [Preprint]. Available at: https://doi.org/10.1109/waina.2015.110.
Pietschmann, C. and Pietschmann, C., 2021. IoT Security Architecture: Trust Zones And Boundaries | Build5Nines. [online] Build5Nines. Available at: